A blog about cloud stuff - by Stian A. Strysse
-
Think about it - if you have access packages governing access to Azure Virtual Desktop, Windows Cloud PC, Citrix, or other remote tools, and new hires need access from day one, managers would historically have to place a manual request to an IGA admin who would then add users to... [Read More]
-
What's lurking in your Microsoft Graph app role assignments?
Gain insights for security and compliance reasons by reporting on all service principals in Entra ID (former Azure AD) having Microsoft Graph app Role assignments.
By Stian A. StrysseI’ve earlier blogged about Building a comprehensive report on admin role assignments in Powershell, this time we’ll look at app role assignments instead. [Read More] -
Defend against MFA phishing of Azure AD user identities
Securing identities in Azure AD with MFA is a no-brainer, but is it really enough? Let's look at attack vectors for the various MFA methods, and how to defend against MFA phishing in Azure AD.
By Stian A. StrysseContinuing on from the Securing user identities in Azure AD beyond MFA blog post, but this time looking at how to prevent MFA phishing attacks. [Read More] -
Follow 'just-enough-access' principle by scoping resources during role elevation in Azure PIM
Utilizing PIM and having no active privileged Azure RBAC or Azure AD roles by default, always requiring 'just-in-time' elevation, is an important risk-reducing strategy. But scoping down access to only the necessary resources during PIM role elevation, adhering to 'just-enough-access', is also best practise. Let's explore how and why.
By Stian A. StryssePrivileged Identity Management (PIM) in Azure is a service that helps organizations to manage, govern and monitor access to resources in Azure and Azure AD. It helps with reducing risk and exposure by adhering to the principle of least-privilege - by providing capabilities for granting privileged access roles to the... [Read More] -
Securing user identities in Azure AD beyond MFA
In today's threat landscape it's important to be healthy paranoid and always re-think how attackers could potentially breach an organization's defenses. So let's explore how to protect user identities in Azure AD beyond MFA
By Stian A. StrysseNo pretty screenshots this time, but I’ll try to keep it short and to the point. [Read More] -
Building a comprehensive report on Azure AD admin role assignments in Powershell
Keeping an eye on Azure AD administrative role assignments is crucial for tenant security and compliance. Forget about the built-in PIM report in the Azure AD portal - take reporting to the next level and build your own report with Graph, KQL and Powershell.
By Stian A. StrysseUnassigning inactive roles, verifying that all role holders have registered MFA and are active users, auditing service principals, role-assignable groups and guests with roles, move users from active to eligible roles in PIM (Privileged Identity Management), and making sure that no synchronized users have privileged roles are just a few... [Read More] -
Query Azure AD logs with KQL from Powershell
Kusto Query Language (KQL) is a powerfull tool to query Azure AD log entries from Log Anayltics in Azure. See how you can query log data using Powershell.
By Stian A. StrysseKQL, short for Kusto Query Language, is really great for quering data sets like Sign-in Logs and Audit Logs in Azure AD. KQL is what Microsoft Sentinel uses under the hood for discovering threats, detections and anomalies in larger data sets. But you can also use it to retrieve simpler... [Read More] -
Granting workload identities least-privilege mailbox access via Microsoft Graph
Workload identities, meaning apps, managed identities and other service principals, can be granted tenant-wide application access to all mailbox resources via Microsoft Graph. Learn how to scope permissions down to specific mailboxes.
By Stian A. StrysseForget about POP3, IMAP, Exchange Web Services (EWS) and other legacy protocols for accessing mailbox resources programmatically. These protocols are being deprecated by Microsoft, and rightly so. See my blog post on blocking legacy authentication for more details. [Read More] -
Connecting to SharePoint Online using Managed Identity with granular access permissions
Microsoft Graph and SharePoint Online supports some granular access permissions using Sites.Selected application scope in Graph, and app access role permissions in Site collections. It even works with Managed Identities.
By Stian A. StrysseThe Sites.Selected application scope was introduced in Microsoft Graph some time ago to support granular app access permissions in SharePoint Online. With this scope one can grant application access to specific SharePoint Online site collections, instead of granting access to all site collections in the tenant, and this is very... [Read More] -
Stop using client secrets and certificates, start using Managed Identities
Managed Identities can be used instead of app client secrets and certificates for Azure resources authenticating to Azure AD. Let's look at what a Managed Identity is and how to use it.
By Stian A. StrysseWhenever an Azure resource needs to authenticate to Azure AD, an identity needs to be provided to the Azure resource. Historically, this process involved creating an App registration with a Service Principal, and adding app credential as a client secret (password string) or a certificate. Then providing the app credential... [Read More] -
Control access to Azure Storage Blobs with Attribute-based Access Control conditions
Let's look at how to configure access to Azure Storage Blobs using Attribute-based Access Control (ABAC) paired with Custom Security Attributes
By Stian A. StrysseLast week I published a blog post describing the basics of Custom Security Attributes, and how it can be utilized paired with ABAC. Now I will dive further into this topic and describe how to get a working configuration with ABAC conditions using Custom Security Attributes for Azure Blobs Storage.... [Read More] -
Block legacy authentication protocols using Azure AD Conditional Access policy
Let's look at blocking legacy authentication protocols in a global company's Azure AD with full control and ease of mind
By Stian A. StrysseI recently worked with a global company to help them tighten the security in their Azure AD tenant, including blocking legacy authentication protocols with Conditional Access policies. Now, blocking legacy authentication isn’t anything new, and there are official Microsoft documentation, guides and blog posts covering this topic, but none the... [Read More] -
Getting started with Custom Security Attributes in Azure AD
This blogpost explores the new Custom Security Attributes public preview feature in Azure AD
By Stian A. StrysseAzure AD has a schema with common attributes for resources like users, e.g. displayName, userPrincipalName, companyName, department and so on. You can also add custom extension attributes via an Application object to extend the schema. However, these attributes are public for all Azure AD users in the organization and should... [Read More] -
Getting started with Custom Extensions in Entitlement Management for Azure AD
Microsoft released a new public preview feature for Azure AD Identity Governance during Ignite this week, namely Custom Extensions for Entitlement Management. Let's dive into what it is and how to use it for identity and access lifecycle management automation.
By Stian A. StrysseCustom Extensions really brings a new flavor to Entitlement Management. Let’s first look at what it is. [Read More] -
Getting started with Azure AD extension attributes
Learn how to add custom extension attributes to Azure AD objects
By Stian A. StrysseIf you need to populate values on Azure AD objects like users and groups, but there are no available attributes in the default Azure AD schema fit for the purpose, an easy solution is to add custom extension attributes to an Application object (app registration) and then populate the attributes... [Read More] -
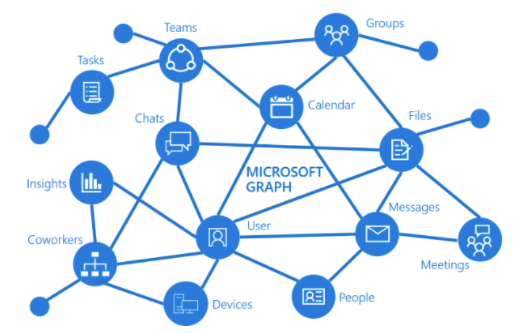
Getting started with Microsoft Graph
Let's go from zero to somewhat hero by getting familiar with topics like REST API, JSON, HTTP methods, access tokens, permission scopes, Graph Exporer, Powershell SDK and more in this blogpost series covering Microsoft Graph.
By Stian A. StrysseIntended for – but not limited to – IT Pros and developers who are familiar with Powershell or other scripting and code languages, who work with Microsoft cloud services, but still haven’t started to look into Microsoft Graph. The goal of this blogpost series is to understand what Microsoft Graph... [Read More] -
Getting started with Microsoft Graph - part 2
The second blogpost in the series explains the Microsoft Graph.
By Stian A. StrysseLet’s continue with this blogpost series by looking at Microsoft Graph! [Read More] -
Getting started with Microsoft Graph - part 3
The third blogpost in the series explains the Graph Explorer.
By Stian A. StrysseLet’s continue with this blogpost series by looking at Graph Explorer! [Read More] -
Getting started with Microsoft Graph - part 4
The forth blogpost in the series explains the Graph Powershell SDK.
By Stian A. StrysseLet’s continue with this blogpost series by looking at Microsoft Graph Powershell SDK! [Read More] -
Getting started with Azure AD App Provisioning and single-sign-on
My first-ever blog post walks through how to configure automated user provisioning and single-sign-on from Azure AD to SaaS apps, specifically for Workplace from Facebook
By Stian A. StrysseAzure AD has many key strengths and features, automated user provisioning and single-sign-on (SSO) capabilities for a number of SaaS apps being two of them. [Read More]